ICMP Packet Sniffing and Spoofing Lab
Introduction
Packet sniffing and spoofing are essential techniques in cybersecurity, used for both network monitoring and penetration testing. This project explores these techniques by implementing various sniffing and spoofing tasks using the Scapy library in Python and the pcap library in C. The goal was to understand how attackers manipulate network traffic and to develop countermeasures against such threats.
Lab Setup
A controlled lab environment was configured using Docker and Oracle VirtualBox running Ubuntu 20.04. The network topology consisted of:
- Host A: Legitimate sender
- Host B: Intended recipient
- Host M: Attacker attempting sniffing and spoofing attacks
All machines were connected within the same subnet, enabling direct ARP and ICMP-based communication.
Tasks and Implementation
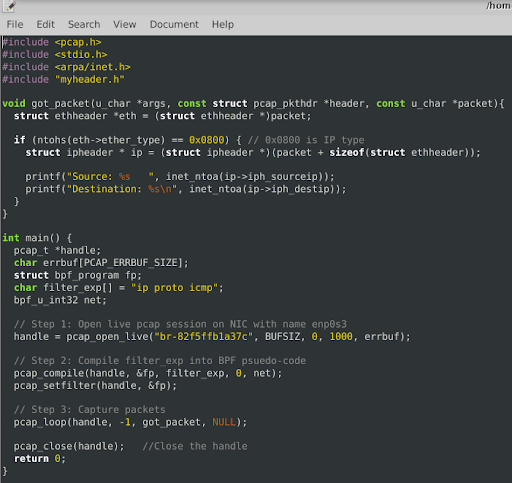
Packet Sniffing and Filtering
This phase focused on capturing and analyzing network packets using Scapy and C with pcap. Filters were applied to isolate ICMP and TCP traffic, allowing for targeted network monitoring.
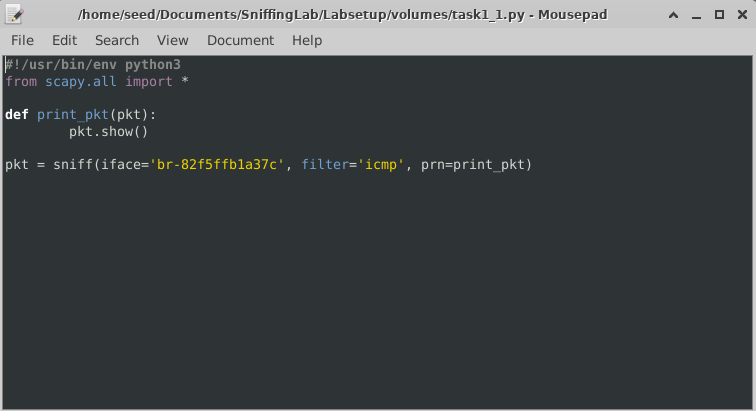
ICMP and UDP Packet Spoofing
Using Scapy and raw sockets, custom packets were crafted to manipulate ICMP echo requests and UDP traffic, demonstrating how attackers forge network communications.
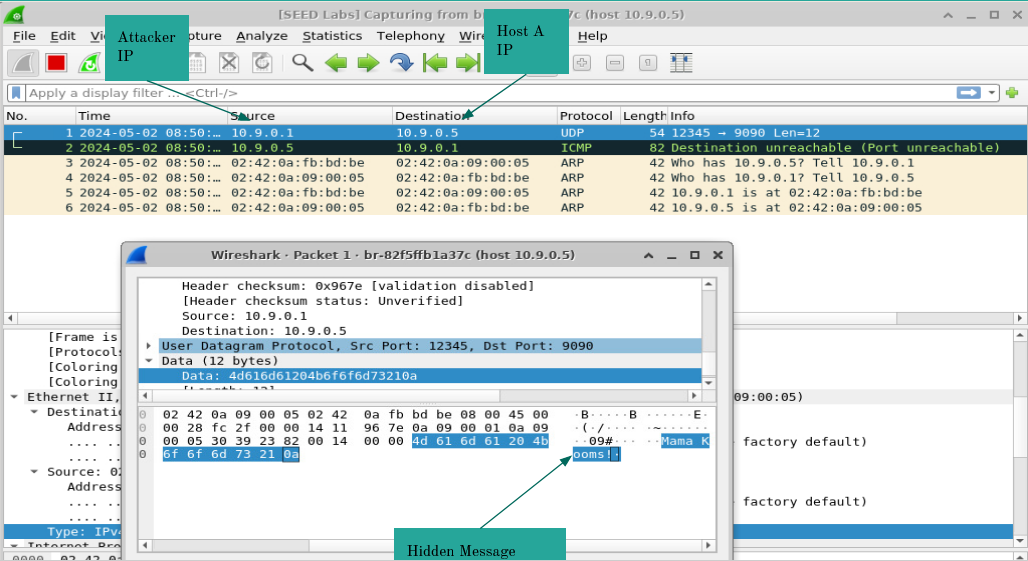
Packet Analysis and Wireshark
Wireshark was used to capture and analyze network packets, allowing for the identification of protocol behaviors, anomalies, and security vulnerabilities in network traffic.
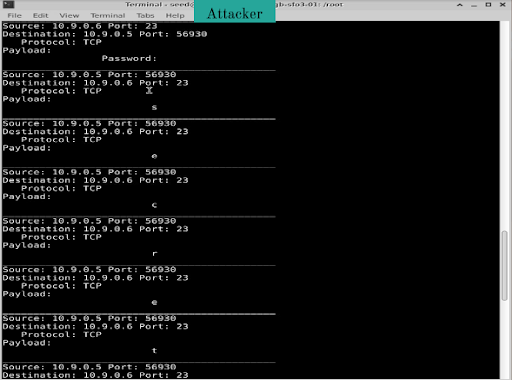
Sniffing and Extracting Sensitive Data
A packet sniffer was created to extract plaintext data from unencrypted protocols such as Telnet, highlighting risks associated with unsecured communications.
Results & Findings
The lab exercises demonstrated how easily an attacker can intercept and modify network packets when security mechanisms are not in place. The major takeaways include:
- Packet sniffing: Capturing network traffic in promiscuous mode allowed visibility into unencrypted communications.
- Packet spoofing: Forged packets successfully misled target hosts into accepting malicious packets.
- Telnet vulnerability: Plaintext passwords were easily extracted from TCP streams, highlighting the need for encrypted communication protocols.
- Root privileges: Running sniffing programs required elevated access due to direct packet manipulation.
Conclusion
This project reinforced the importance of network security measures such as encryption, secure protocols, and intrusion detection systems. Understanding packet sniffing and spoofing techniques provides insight into securing networks against similar threats.
References
- Scapy documentation. (n.d.). https://scapy.readthedocs.io/en/latest/
- Wireshark Packet Analysis. (n.d.). https://wiki.wireshark.org/
- Pcap Library Documentation. (n.d.). https://www.tcpdump.org/
- Full Writeup: Source